Cyber risk has become more than a technical issue. It’s a business reality with contractual, financial, and reputational stakes. For mid-sized organizations, that pressure often lands on the IT director or MSP partner, who’s suddenly expected to handle compliance, vendor assessments, and board-level risk reporting all on top of keeping the lights on.
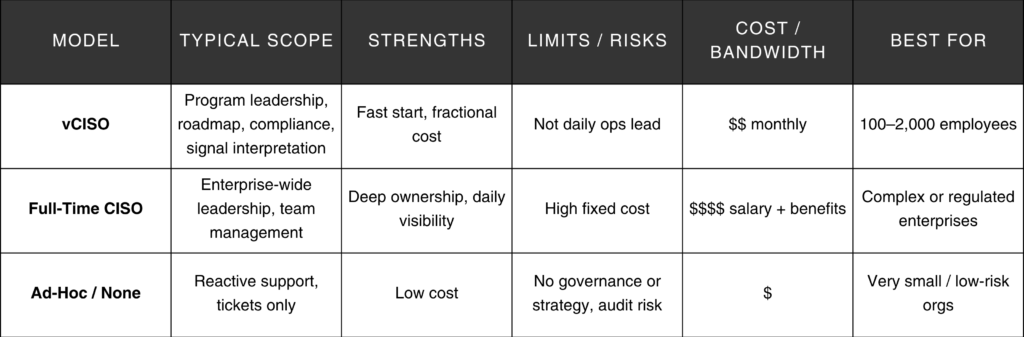
A Virtual Chief Information Security Officer (vCISO) bridges that gap. If your organization has between 100 and 2,000 employees and you’re navigating frameworks like ISO/IEC 27001:2022, NIST CSF 2.0, PCI DSS v4.0, or HIPAA, a vCISO can bring the necessary structure, expertise, and measurable results to your cybersecurity program.
With a vCISO, you’ll get executive-level security leadership, covering governance, compliance, and strategy without the overhead of hiring a full-time, in-house CISO.
Book a Consult to see how IT Solutions’ vCISO services can align your security posture with your business goals.
The Business Problem a vCISO Solves
Many growing organizations share the same set of challenges:
- Escalating audits and customer questionnaires: without anyone clearly accountable for security governance.
- Tool sprawl and alert fatigue: multiple dashboards, limited insight, and no defined roadmap.
- Budget pressure: to deliver security outcomes without expanding headcount.
A vCISO answers those challenges by owning the program leadership role, turning scattered efforts into a measurable, framework-aligned strategy.
Learn more about our Cybersecurity Services.
What Does a vCISO Do?
A vCISO provides executive-level security leadership on a fractional basis, defining strategy, governing risk, aligning controls, and translating security data into clear business decisions.
A professional serving in a vCISO capacity will oversee:
- Security charter and program governance structure
- Risk register and risk appetite definition
- Policy stack and control mapping to standards
- Vendor/third-party risk assessments
- Incident Response Plan (IRP) and tabletop exercises
- KPI and board-level reporting (e.g., MTTD, MTTR, control coverage)
Five Reasons to Choose a vCISO
- Optimize Existing IT and Security Investments: A vCISO helps you get more from the tools and services you already own. Instead of recommending a costly rip-and-replace, they rationalize your SIEM, EDR/XDR, IAM, and email security stack, eliminating redundancy and improving return on investment.
- Support Compliance and Audit Readiness: A vCISO ensures you have documented controls, evidence plans, and a path to continuous compliance, whether your customers require ISO 27001, NIST CSF, PCI DSS, or HIPAA.
- Strengthen Posture with a Defined Security Roadmap: A vCISO provides proactive direction through 90-day and quarterly roadmaps that outline risks, owners, budgets, and prioritized improvements.
- Gain Strategic Insight from Security Signals: A vCISO interprets SOC and SIEM data, Dark Web findings, and vulnerability reports, distilling them into actionable intelligence that reduces noise and speeds response.
- Get Board-Level Leadership Without the Full-Time Overhead: A full-time CISO can exceed $250,000 annually. A vCISO delivers comparable executive direction at a fraction of the cost while still providing ongoing oversight and quarterly reporting.
Do We Need to Start from Scratch?
No. A vCISO improves what’s already in place, from your policies and tools to your processes. From there, they identify quick wins and prioritize gaps that deliver immediate improvement.
Early activities include:
- Tool rationalization and configuration review
- Policy refresh and alignment to frameworks
- Identification of top-10 security gaps
- Quick-win initiatives for measurable risk reduction
What Size Company Needs a CISO or vCISO?
A vCISO offers the right balance for most small-to-mid-sized organizations, bringing expert guidance while providing measurable outcomes and lower fixed costs compared to a full-time CISO.
If you’re facing customer security audits, handling regulated data, expanding into the cloud, or have experienced a recent incident, you need a CISO-level function.
vCISO vs. Full-Time CISO vs. Ad-Hoc IT
How to Start with a vCISO
90-Day Checklist
- Confirm your drivers: audits, contracts, recent incidents, or customer demands.
- Define success metrics such as MTTD, MTTR, audit milestones, or control coverage.
- Baseline your controls against your chosen framework (CSF 2.0, ISO 27001, PCI DSS, HIPAA).
- Identify top 10 gaps and assign ownership.
- Develop a Security Roadmap with prioritized initiatives, timelines, and budgets.
- Set up a risk register and establish a monthly operations cadence with quarterly board reporting.
- Review SOC/SIEM and Dark Web findings, translating insights into defined playbooks and ticket workflows.
By day 90, you’ll have an executable plan tied to your business outcomes with a fully operational governance structure and documented risks.
Risks and Trade-offs
- Misaligned expectations: Start with a written charter and defined KPIs.
- Over-automation: Maintain human oversight for high-impact actions to avoid policy drift.
- Tool sprawl persistence: Adding new tools isn’t always the answer. Commit to rationalization.
- Daily presence: A full-time, in-house CISO may be more appropriate if you need someone on-site managing a large team.
When to Get Expert Help
If you’re preparing for your first major compliance audit, struggling with vendor questionnaires, or need a roadmap your leadership team can understand, a vCISO engagement delivers clarity and measurable progress.
Book a vCISO Readiness Consult and start building your 90-day plan today.
Frequently Asked Questions
- What specific deliverables should we expect in the first 90 days?
- A program charter, risk register, updated policy set, SOC/SIEM and Dark Web reviews, KPI dashboard, and a board-ready summary.
- Will a vCISO replace our MSP or IT team?
- No. The vCISO provides governance and strategy, while your MSP or IT staff executes tactical activities under that direction.
- How do you measure success?
- Success is tracked through framework-aligned milestones, including audit readiness, MTTD/MTTR reduction, control coverage, and closure of vendor risks.

