The Cybersecurity Maturity Model Certification (CMMC) is how the U.S. Department of Defense (DoD) verifies that contractors protect FCI (Federal Contract Information) and CUI (Controlled Unclassified Information). It shows up in contract language and gets phased into awards. The DoD is enforcing these requirements as of November 10, 2025 so if you don’t meet the designated level and record it in SPRS you can be ruled ineligible, losing out on business.
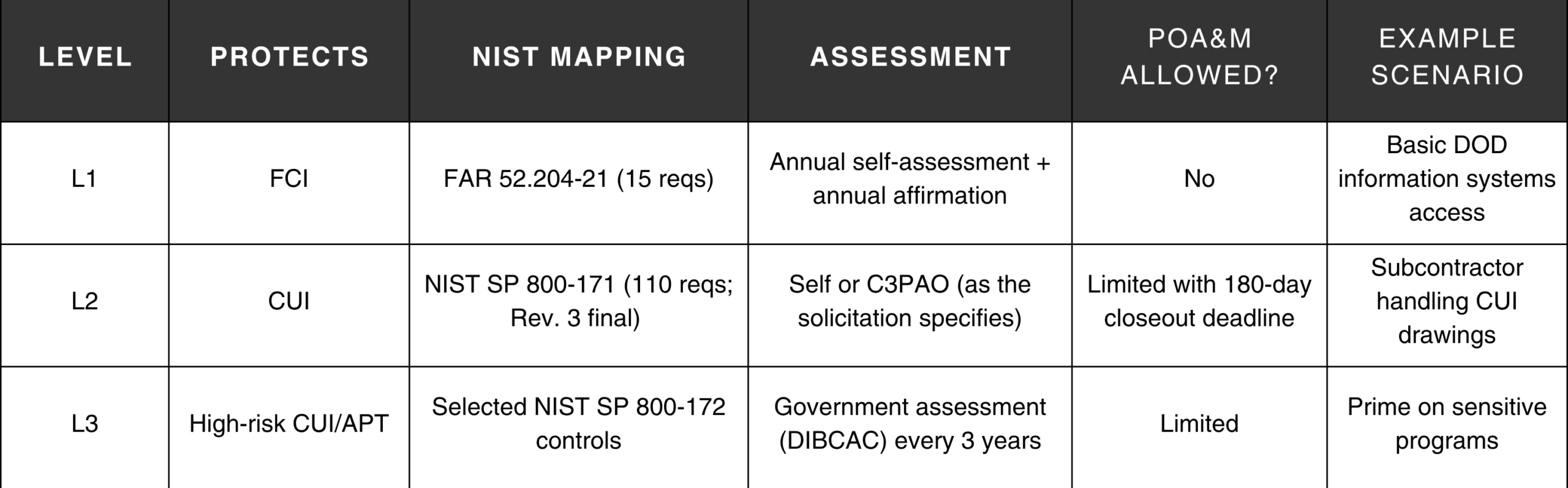
- Three levels map to the sensitivity of what you touch: basic FCI (Level 1), CUI (Level 2), and higher-risk programs (Level 3).
- The final rule codifies CMMC at 32 CFR Part 170 and became effective December 16, 2024, with a phased rollout over three years via DFARS clauses.
Which CMMC level do I need?
If you only handle FCI, you’re generally looking at Level 1 with an annual self-assessment. If you handle CUI, you’ll need Level 2 (sometimes self-assessment, sometimes a C3PAO). The most sensitive work is Level 3, assessed by the government (DIBCAC). Always check the solicitation and flow-downs.
- FCI (Level 1): information provided or generated for the Government under a contract that isn’t intended for public release (safeguarded under FAR 52.204-21).
- CUI (Level 2): unclassified information requiring safeguarding per 32 CFR Part 2002 and the NARA CUI Registry (category definitions/markings).
- High-risk CUI/APT (Level 3): selected enhanced protections from NIST SP 800-172 with a government (DIBCAC) assessment every 3 years; limited POA&Ms and stricter evidence expectations. NIST SP 800-172; DoD DIBCAC.
CMMC levels at a glance
Book Consult | Explore our Cybersecurity Services
How CMMC relates to NIST SP 800-171 Rev. 3
Right now, CMMC Level 2 is still formally mapped to NIST SP 800-171 Rev. 2 in DoD documentation and contracts. Rev. 3 has been finalized, but it has not yet been formally enforced by DoD for CMMC purposes. Most observers expect Rev. 3 to become the required baseline in a future rule or update.
In practical terms, that means:
- Level 2 = NIST SP 800-171. To pass Level 2, you implement the 110 requirements in 800-171 Rev. 3 and show your work using 800-171A assessment procedures.
- Level 3 adds 800-172. That’s where the DoD pulls in targeted, enhanced protections for programs facing more advanced threats.
- Level 3 adds selected enhanced protections from NIST SP 800-172 for programs at higher risk from APTs.
Where IT Solutions fits in: We focus on Level 1 and Level 2. We begin with a CMMC Compliance Gap Assessment to outline the project area (usually by separating a CUI enclave to reduce effects), find areas where you don’t meet the current standard, and give you a list of important recommendations and actions to take next. Following the assessment, our vCISO Cybersecure Regulatory team can partner with you to strategically close gaps, mature your security program, and help you move toward CMMC certification.
Do I need a third-party assessment (C3PAO)?
Level 1 is an annual self-assessment. Level 2 can be a self-assessment or a C3PAO certification, depending on contract demands. Level 3 is assessed by DIBCAC (a DoD team), not a C3PAO. If you’re bidding soon, verify the assessment type now to avoid a schedule crunch.
A couple of practical notes:
- Cyber AB maintains the C3PAO marketplace.
- Even for self-assessments, keep your evidence organized because you’ll need it for SPRS and potential government validations.
Timelines & Rollout
The CMMC rule was finalized in September 2025 and is enforceable as of November 10, 2025, with a three-year phased rollout across new DoD contracts. Your timeline depends on current 800-171 gaps, how quickly you can harden controls, how fast you can produce evidence, and, if required, when you can get on a C3PAO calendar. Count on several months for remediation plus assessor lead time.
The reality for most Level 2 teams:
- Gap closure: Often measured in months, not weeks, especially for identity, logging, incident response, and vulnerability management.
- Assessment lead times: If a C3PAO is required, book early.
- POA&M windows: Limited and time-boxed; don’t count on long grace periods.
How to get ready
Readiness Steps
- Scope your world. Identify whether you handle FCI, CUI, or both. Draw a hard boundary for in-scope systems; consider a CUI enclave to minimize disruption elsewhere.
- Conduct a compliance gap assessment. Work with your IT vendor to compare your current practices to NIST 800-171 Rev. 3, document results in your SSP and POA&M using 800-171A methods, and get a prioritized remediation roadmap.
- Prioritize the big rocks. MFA everywhere it should be, good logging and monitoring, incident response you can actually execute, strong access control, and a living vulnerability management rhythm.
- Post (and maintain) your SPRS score. Use PIEE to record your 800-171 self-assessment score. Contracting officers check it.
- If required, schedule the assessment. For Level 2 solicitations that mandate certification, line up a C3PAO and prep objective evidence. Level 3 is DIBCAC territory.
- Close POA&Ms fast. They’re allowed in limited fashion and on a clock. Track owners and due dates.
- Sustain. Plan on 3-year certification cycles (where applicable), plus annual affirmations, and keep your artifacts fresh.
Want a quick reality check on scope, score, and schedule? Book Consult
SPRS, DFARS clauses, and your bid status
- SPRS is the scoreboard. It’s where your 800-171 score (and, when applicable, CMMC status) lives. No current score/affirmation when the clause applies? Expect trouble at award time.
- DFARS 252.204-7019/7020/7021 are the levers that make this real in solicitations and subcontracts. They call for SPRS posting, potential government assessments, and, when required, a current CMMC certificate.
- Flow-down matters. If you’re a prime, your suppliers can become your risk. If you’re a sub, expect primes to pressure-test your status.
Risks & trade-offs
- Eligibility risk: Missing the required level or a current SPRS entry can knock you out of the running.
- Budget & time: Remediating to Rev. 3, producing evidence, and scheduling an assessment can be non-trivial, so plan accordingly.
- Scope strategy: Enterprise-wide compliance vs a CUI enclave is a classic “cost vs friction” decision.
- Supply chain: Requirements flow down. Vet subs early or your weakest link can become a blocker.
When to bring in help
If you touch CUI, have a low or negative SPRS score, or you’ve got a near-term bid, it’s time. We’ll map DFARS and NIST to a concrete plan, including scope, enclave design, SSP/POA&M, and evidence collection, and help you coordinate with a C3PAO when certification is required.
Book a CMMC Readiness Consult
Frequently Asked Questions
- What is SPRS and why does it matter?
- It’s the Supplier Performance Risk System, where your NIST 800-171 score (and CMMC status) is recorded. Contracting officers look there to confirm eligibility and risk posture.
- What’s the difference between FCI and CUI?
- FCI is non-public contract information that must be safeguarded under basic controls. CUI is unclassified but sensitive information with stricter handling rules. Handling CUI will often trigger CMMC Level 2.
- Are POA&Ms allowed?
- Yes, but only in a limited way at Levels 2/3 and with tight closeout windows. Don’t rely on POA&Ms for foundational controls.
- Does Level 2 always require a C3PAO?
- We use ITIL-aligned change enablement: categorize risk, require approvals, schedule windows, and define backout plans. Post-change reviews feed continuous improvement.
- How do Ontario regulations affect our stack?
- Not always. Some Level 2 awards accept a self-assessment; others require a C3PAO. The solicitation is the source of truth so confirm early.