Introduction
In today’s digital age, cybersecurity is not merely a technological concern—it is a critical business imperative. This is particularly true for small and medium-sized businesses (SMBs) operating within the U.S. defense industrial base (DIB).
To safeguard sensitive defense information, the U.S. Department of Defense (DoD) has implemented the Cybersecurity Maturity Model Certification (CMMC) framework. Compliance with the CMMC framework is mandatory for defense contractors and their subcontractors, but achieving compliance can be a daunting challenge for businesses with limited resources and expertise.
Managed Service Providers (MSPs) often play a crucial role in empowering businesses to meet compliance requirements through CMMC Level 1 and Level 2 assessments to navigate this complex landscape and obtain (and maintain) CMMC compliance.
The CMMC Framework: A Brief Overview
The CMMC framework establishes a tiered approach to cybersecurity maturity, ranging from Level 1 (Basic Cyber Hygiene) to Level 5 (Advanced/Progressive). Each level comprises specific security practices and processes that organizations must implement to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
- Level 1: Basic Cyber Hygiene focuses on safeguarding FCI (information not intended for public release that is provided or generated under a government contract) and implementing fundamental cybersecurity practices.
- Level 2: Intermediate Cyber Hygiene builds upon Level 1 by adding additional security requirements for protecting CUI (information that is more sensitive than FCO and requires stricter security controls).
CMMC Compliance Poses Challenges to Businesses
Businesses often face significant hurdles in achieving CMMC compliance, such as:
- Limited Resources: Organizations often lack the financial resources and in-house expertise to implement and maintain the necessary security controls to meet CMMC compliance.
- Complexity: Understanding and interpreting CMMC requirements can be overwhelming, particularly for organizations without dedicated IT or security personnel.
- Time Constraints: Meeting rigorous CMMC deadlines while balancing other business priorities can be challenging.
- Ongoing Maintenance: CMMC compliance is not a one-time event—it requires continuous monitoring, assessment, and improvement.
The MSP Advantage
A mature MSP will serve as a trusted partner and offer invaluable support to businesses that are embarking on (or managing) a CMMC compliance journey:
- Expertise: MSPs with robust security capabilities, like IT Solutions, possess the technical knowledge and experience to assess your current security posture, identify gaps, and develop a remediation plan.
- Cost-Effectiveness: In many cases, outsourcing CMMC compliance to an MSP is more cost-effective than hiring and training internal staff.
- Scalability: Mature MSPs can scale their security services to meet your changing needs as you grow and evolve.
- Proactive Management: MSPs with an adequate security portfolio provide ongoing monitoring and management of security controls to ensure you experience continuous compliance and peace of mind.
- vCISO Integration: Some MSPs offer a designated Virtual Chief Information Officer (vCISO), who will provide strategic guidance and oversight and help you develop and implement a tailored yet comprehensive cybersecurity program.
Added Benefits of vCISO Integration with an MSP
Partnering with a mature MSP that provides a designated vCISO in conjunction with CMMC assessment services significantly simplifies obtaining CMMC compliance:
- Streamlined Compliance: Your vCISO guides you through the CMMC assessment process, helping you to fill in the gaps and ensure all compliance requirements are met.
- Strategic Guidance: A vCISO provides executive-level expertise and guidance on cybersecurity strategy, aligning security with your business goals.
- Risk Mitigation: By identifying and addressing vulnerabilities, your vCISO reduces the risk of data breaches and cyberattacks.
- Continuous Improvement: vCISOs help maintain and improve your security posture through ongoing monitoring and management.
- Peace of Mind: Focus on your core operations, knowing that your business’ security and compliance are in the capable hands of a vCISO.
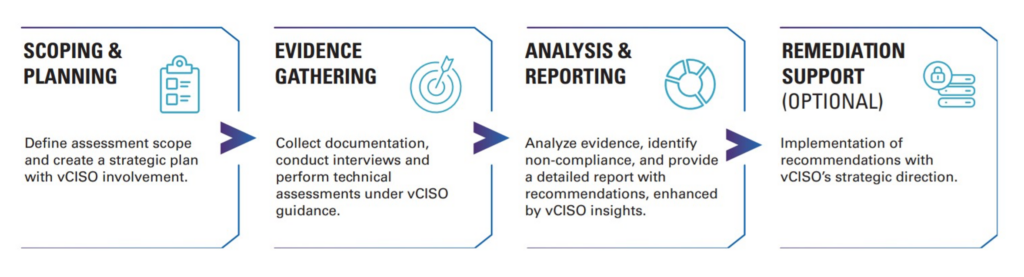
CMMC Assessment Services — IT Solutions’ Proven Process
At IT Solutions, we provide CMMC Level 1 and Level 2 Assessment Services. Our proven process (outlined below) demonstrates how involved and critical a vCISO can be in obtaining and managing CMMC compliance.
For instance—if you partner with IT Solutions for CMMC Assessment Services, your vCISO will conduct a thorough evaluation of your environment, carefully assessing policies, procedures, and technical control to proactively identify vulnerabilities and opportunities for improvement. From that, your vCISO provides executive-level guidance to ensure alignment with industry best practices and meet regulatory requirements.
Negative Consequences of Non-Compliance
Failure to achieve CMMC certification can have severe repercussions for organizations in the DIB:
- Loss of Contracts: Non-compliant organizations may be disqualified from bidding on or winning government contracts.
- Financial Penalties: The DoD may impose significant fines or penalties for noncompliance.
- Reputational Damage: A data breach or cybersecurity incident can devastate an organization’s reputation and erode customer trust.
- Legal Liability: Organizations may face legal action for failing to protect sensitive governmental information.
Key Takeaways
- CMMC compliance is essential for organizations in the DIB, but it can be a complex and challenging process.
- A mature MSP with a focus on security, like IT Solutions, can offer a streamlined solution that provides the expertise, resources, and support needed to navigate the CMMC framework and achieve compliance.
- By partnering with IT Solutions, businesses can strengthen their security posture, mitigate risks, and confidently pursue government contracts.
- The cost of non-compliance is simply too high, making the investment in CMMC compliance a strategic imperative for any organization operating in the DIB.


